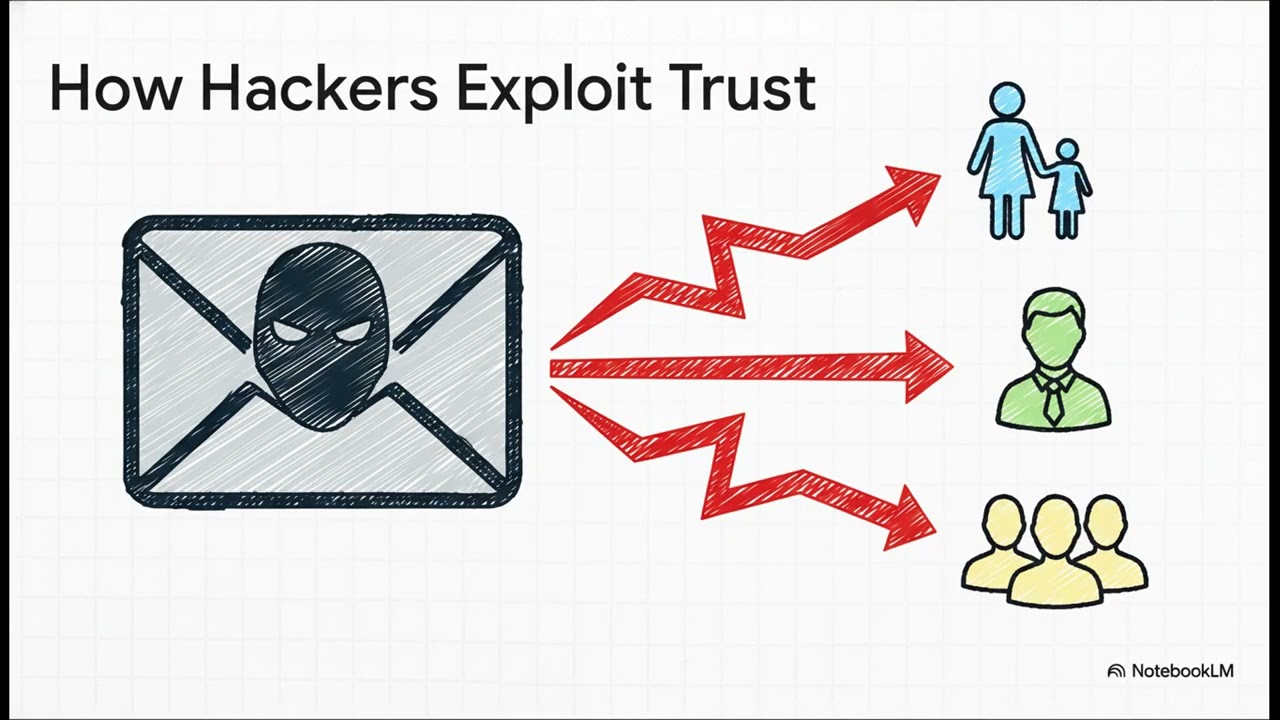
In today’s hyperconnected world, your *email address* is more than just a way to send messages — it’s a key that unlocks your entire digital identity. This in-depth guide, “Why a Hacker Would Use Your Email to Impersonate You,” explores the hidden reasons cybercriminals target personal emails to access, exploit, and impersonate real users online.
Hackers know that email is often the gateway to social media, financial accounts, and cloud storage. By pretending to be you, they can manipulate your contacts, reset your passwords, and gain access to sensitive information — all without you realizing it until it’s too late. This article breaks down the *six most common motives* behind hacker email impersonation:
1️⃣ *Credibility and Trust* – Hackers use your familiar email address to make scams and phishing messages look legitimate.
2️⃣ *Account Chaining* – Once inside, they can request password resets or access linked accounts like Facebook, Instagram, or banking apps.
3️⃣ *Data Harvesting* – Impersonation allows them to collect personal and professional information about you and your network.
4️⃣ *Spreading Malware or Scams* – By posing as you, hackers can send infected links or files that trick others into downloading malware.
5️⃣ *Covering Tracks* – Using your identity helps attackers hide their true location and avoid detection.
6️⃣ *Reconnaissance* – They test your defenses to prepare for larger-scale breaches or identity theft.
The article also provides *actionable cybersecurity tips* to safeguard your personal data, such as using strong, unique passwords, enabling two-factor authentication (2FA), monitoring unusual login attempts, and being cautious with unfamiliar links or attachments.
If you’ve ever wondered *why someone would target your email*, this guide reveals exactly how and why hackers exploit email-based impersonation — and how you can fight back. Protect your privacy, secure your digital footprint, and learn the signs of hacker activity before it’s too late.
📘 Read the full article here:
👉 [https://moderntechandsecurity.blogspot.com...](https://moderntechandsecurity.blogspot.com...)
🔑 SEO Keywords:
email impersonation, hacker email tactics, email security, identity theft protection, social engineering, phishing scams, cybersecurity awareness, hacked accounts, online privacy, data protection, account takeover, malware prevention, 2FA security, hacker disguise methods, protect your email
@EbookScribe713

Информация по комментариям в разработке