This paper was presented by Himanshu Anand and Chastine Menrige (Symantec) at VB2016 in Denver, CO, USA.
In the last year, there has been growing interest in a technique known as fileless infection, where malware authors compromise computers without writing any files to disk. This technique allows the threat to evade detection from file-scanning software while still remaining persistent.
This paper will explain the different fileless infection methods, as well as a new tactic which can allow attackers to perform fileless infection using a classic one-click fraud attack and non-PE files.
Traditional malware is contained in a file on disk. A registry run key links to this file in order to make the threat persistent. With a fileless infection, the malware does not exist on the compromised computer as a normal file. Instead, it is located in a subkey within the computer's registry as a script, such as Windows PowerShell, VBScript, or JavaScript. The payload in the registry is called every time Windows starts.
The one-click fileless infection technique we've seen uses JavaScript, though different scripts could also work. The infection arrives on the computer through an .hta file, which places the JavaScript payload into a registry subkey. The JavaScript code can be triggered every time Windows starts by calling: rundll32.exe javascript:"\..\mshtml,RunHTMLApplication ";alert('payload');
The JavaScript code can read and decode encoded data from another subkey. This data injects the payload into memory. Every few minutes, the payload checks for its registry entry. If the entry has been deleted, then the payload recreates it so that the infection remains persistent.
The first widespread threat we saw using the fileless infection technique was Trojan.Poweliks in 2014. Many other trojans followed suit as they evolved: Trojan.Bedep and Trojan.Kovter adopted the same technique after Poweliks.
Based on our research, the most common infection vectors for this technique include the following:
Drive-by downloads / Exploit kits: In August 2014, the Angler EK became the first kit to infect a computer without writing the malware on the disk. Instead, the malware was injected directly into the process running the exploit plug-in. Over time, we have seen more instances of fileless infections using this infection vector.
Downloaders: Through this method, the downloader is written onto disk. Once it gets executed, it will retrieve the final payload and may delete itself. The final payload remains in memory, acting as the fileless infection.
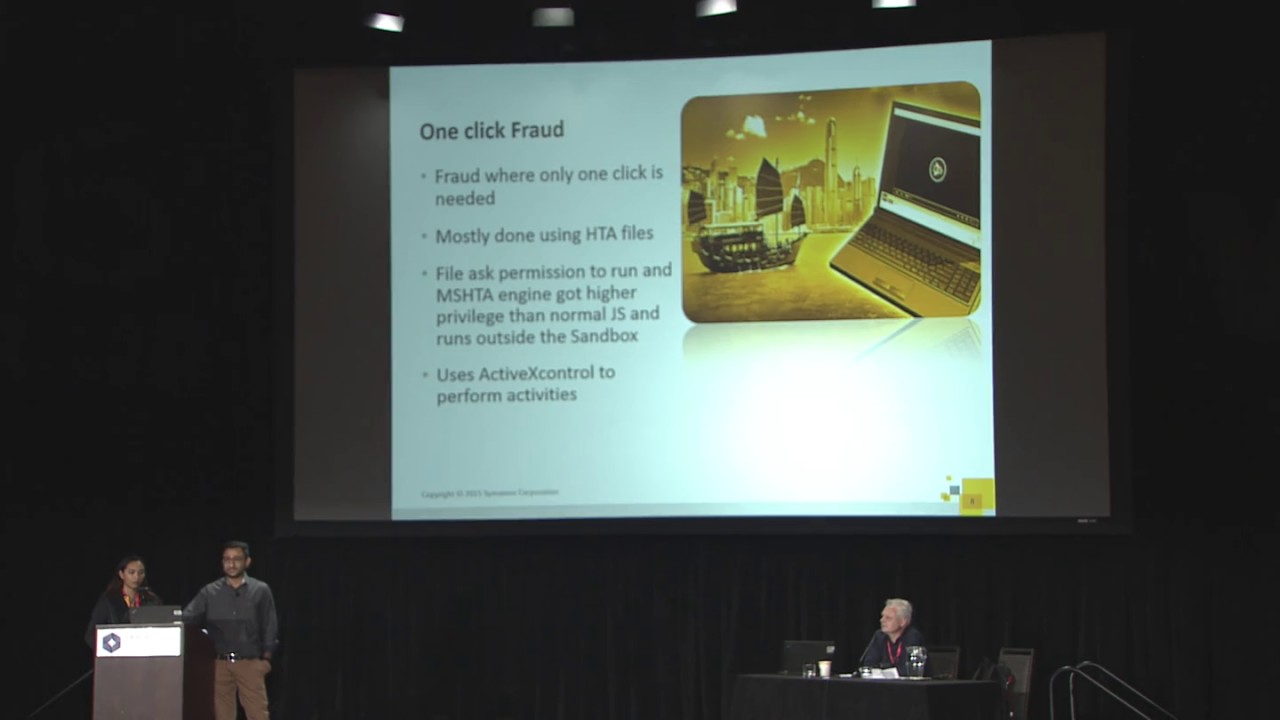
One-click fraud: One-click fraud, which mostly targets Japanese and Chinese users, tricks a user into clicking a tempting offer. If this works, then a malicious file is downloaded onto the computer without the user's knowledge. The threat displays annoying/obscene pop-ups and asks the user to pay to remove them, in a similar manner to ransomware. A variant of Kovter, which is known for click-fraud, included fileless infection capabilities. While we haven't seen many threats conducting one-click fraud in a fileless manner, sooner or later attackers may engage in this method, as it is PE-free, exploit-free, and harder to detect. This is something that our paper will explore.
Our paper will explain and compare the most common ways in which malware authors use fileless infections today. We will discuss areas where we expect these methods to be used soon.

Информация по комментариям в разработке