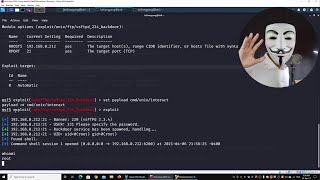
Dive into the world of ethical hacking with our comprehensive guide on Metasploit! Learn how this robust toolkit helps security professionals identify vulnerabilities by simulating real-world attacks. We’ll walk you through setting up a safe environment using VirtualBox and a pre-built Metasploit virtual machine image, ensuring you practice hacking skills responsibly. Understand the intricacies of payload creation, handler configuration, and secure, ethical penetration testing. Emphasize the importance of obtaining explicit consent, defining the scope, and handling vulnerability information responsibly. Become a cybersecurity professional committed to making the digital world safer. Like & share this video to spread awareness about ethical hacking!
#Metasploit #EthicalHacking #Cybersecurity #PenetrationTesting #VirtualBox #Payloads #CyberSafety #InfoSec
OUTLINE:
00:00:00 A Hacker's Toolbox
00:01:51 Setting Up Your Metasploit Lab
00:02:35 Crafting Your Android Payload
00:04:26 Setting Up a Metasploit Handler
00:06:17 Getting it onto the Device
00:06:56 Basic Post-Exploitation Commands
00:07:35 The Rules of Engagement
00:08:10 Don't Cross the Line
00:08:54 What to Do with Your Findings
00:09:34 The Power and Responsibility of Penetration Testing
00:10:17 Level Up Your Security Skills with Metasploit
YouTube Tags
1. Metasploit
2. Android Hacking
3. Cybersecurity
4. Penetration Testing
5. Ethical Hacking
6. Kali Linux
7. Mobile Security
8. Metasploit Framework
9. Android Exploits
10. Cybersecurity Training
Keywords
1. Metasploit Android
2. Hack Android
3. Android Penetration Testing
4. Mobile Hacking
5. Metasploit Tutorial
6. Android Security
7. Ethical Hacking Tools
8. Kali Linux Metasploit
9. Android Vulnerabilities
10. Mobile Security Testing
Hashtags
1. #Metasploit
2. #AndroidHacking
3. #Cybersecurity
4. #PenTest
5. #EthicalHacking
6. #KaliLinux
7. #MobileSecurity
8. #AndroidExploits
9. #CyberSec
10. #HackLikeAPenTester
Metasploit, Android Hacking, Penetration Testing, Cybersecurity, Mobile Security, Metasploit Framework, Android Exploitation, Mobile Pen Testing, Metasploit Tutorial, Android Vulnerabilities, Ethical Hacking, Security Testing, Android Pentesting, Metasploit Android, Mobile Security Testing, Android Security, Metasploit Android Exploitation, Mobile Hacking, Android Penetration Testing, Metasploit Framework Android, Mobile Security Research, Android Security Testing, Metasploit Android Tutorial, Mobile Security Tools, Android Vulnerability Assessment, Metasploit Android Exploits, Mobile Security Best Practices, Android Security Best Practices, Metasploit Android Vulnerabilities, Mobile Security Training, Android Security Training, Metasploit Android Training, Mobile Security Hacking, Android Security Hacking, Metasploit Android Hacking, Mobile Security Tools and Techniques, Android Security Tools, Metasploit Android Tools, Mobile Security Techniques, Android Security Techniques, Metasploit Android Techniques, Mobile Security Testing Tools, Android Security Testing Tools, Metasploit Android Testing Tools, Mobile Security Testing Techniques, Android Security Testing Techniques, Metasploit Android Testing Techniques.








Информация по комментариям в разработке