more information : https://instagram.com/official__nonu1...
ZShadow.com or Z Shadow Hacker is an online tool used to hack various social network accounts like Facebook, Twitter, Instagram, Gmail, Yahoo, Hotmail, etc. This online hacking service is provided by Zshadow.com. This page will guide you on how to use the Zshadow.com website to gain access to someone’s Social Accounts Id using Zshadow.com in 2021.
Every month more than 250,000 people search the term “ ZShadow.com | Z Shadow Login My Account ”. This is something becoming very popular day by day. Everyone has their own reason for hacking someone’s account, some do it for fun, some for purpose of revenge, etc.
Before sharing more details about this amazing Zshadow.com website, we highly recommend you to watch this video on how to use Z Shadow hacker.
Using the Z-Shadow hacker is one of the free, easy, and simplest methods of hacking Facebook and Gmail accounts in just a few minutes.
Therefore, today I am writing a complete step-by-step guide on how to use ZShadow.com to hack Instagram accounts. It is the official ZShadow.com guide to hack Facebook ID and Gmail accounts and various Other Social Accounts.
These days, Social Media have become a significant need in our everyday life. It encourages us to associate and connect with anyone over the world. We share our day to day routine, private life, and our financial details with our followers. That is the reason; malicious hackers pick social media platform for hacking because they get every single aspect of an individual without any problem.
We are living in an era where technological advancements are rapidly flourishing, despite people having non-technical backgrounds are unable to pay attention to how to secure their data from malicious hackers. Around the world, there are currently 2.8 million cybersecurity professionals who have complete knowledge of malicious hacking and how to prevent it. Unfortunately, that is a minimal number related to how many people are using social media, giving their day to day information on these platforms, which are prone to cyber-attacks.
Table of Contents
How Hacker Accesses Your Social Media Account
Man in the Middle Attack
Phishing Attack
DNS Spoofing/ Cache Poisoning Attack
Cookie Hijacking
Keylogging
How Hacker Accesses Your Social Media Account
In this article, I will explain each tactic of a malicious hacker so that you will get an idea of how these hackers can hack social media accounts. These are the most common attacks a hacker can perform:
Man in the Middle Attack
Man in the Middle Attack
This type of attack occurs when a hacker privately steals and alters the communication between the sender and receiver. A user may think he is communicating with a legitimate user, but actually, all the conversation is passing through hacker, and he possibly alters their communication without their knowledge.
For this purpose, BurpSuite is the commonly used tool by hackers to perform a man in the middle attack. By using this tool, hackers can intercept between the machine and a server, captures the request that is generated by machine to the server, and alters it by requesting another thing from the server.
Prevention
Always use a good antivirus with a firewall that can detect the fake user. Besides, use VPN and Proxy server to access the network.
Phishing Attack
DNS Spoofing/ Cache Poisoning Attack
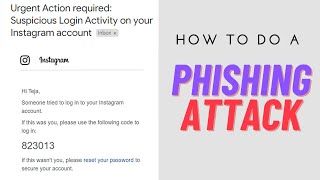
Phishing is the most common yet most effective tactic used by hackers to fool people and steal their information. In this attack, a hacker will make a fake social media login page that looks legitimate and share it with victims to get login from a fake site. When a victim enters its credentials, it directly redirects to the hacker’s machine. This is the most effective technique because many users can not differentiate between the real and fake sites’ login pages and get fooled by giving their credentials. This attack requires persistence and excellent skills for making the victim login from your duplicate fake page.





![GIT - Полный Курс Git и GitHub Для Начинающих [4 ЧАСА]](https://i.ytimg.com/vi/O00FTZDxD0o/mqdefault.jpg)


Информация по комментариям в разработке